[Infographic] Healthcare Cyber Security: Threat Prognosis
•
2 j'aime•1,427 vues
FireEye provides cybersecurity solutions for healthcare organizations. The document discusses how healthcare organizations suffer data breaches frequently and that regulatory compliance is not sufficient for protection against modern cyber attacks. All healthcare organizations that experienced breaches in 2014 were compliant with security standards. The annual cost of data breaches for the healthcare industry is $6 billion and the 10 largest healthcare cyber attacks of 2015 affected over 111 million records. Stronger cybersecurity is needed to protect against financial losses from breaches, lawsuits, and system damage.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Contenu connexe
Tendances
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breachesThe Economist Media Businesses
Tendances (20)
Cybersecurity Facts & Figures - What Every Business Needs to Know

Cybersecurity Facts & Figures - What Every Business Needs to Know
Identifying and securing areas of the business you may have never considered ...

Identifying and securing areas of the business you may have never considered ...
The Top Five Essential Cybersecurity Protections for Healthcare Facilities

The Top Five Essential Cybersecurity Protections for Healthcare Facilities
The Security of Electronic Health Information Survey

The Security of Electronic Health Information Survey
CBIZ Cyber Security - What Every Business Needs to Know

CBIZ Cyber Security - What Every Business Needs to Know
Cost of Cybercrime Study in Financial Services: 2019 Report

Cost of Cybercrime Study in Financial Services: 2019 Report
Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS

Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
Sharing the blame: How companies are collaborating on data security breaches

Sharing the blame: How companies are collaborating on data security breaches
5 email management systems protect yourself from spam, viruses, malware an...

5 email management systems protect yourself from spam, viruses, malware an...
En vedette
En vedette (13)
Sodexo Offshore infographic: result of our 2014 global survey

Sodexo Offshore infographic: result of our 2014 global survey
Соответствие между тех. специализациями и продуктами Trend Micro. 17 ноября 2011

Соответствие между тех. специализациями и продуктами Trend Micro. 17 ноября 2011
Healthcare Security Essentials jean pawluk april 28 2011 

Healthcare Security Essentials jean pawluk april 28 2011
Similaire à [Infographic] Healthcare Cyber Security: Threat Prognosis
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...The Lifesciences Magazine
Similaire à [Infographic] Healthcare Cyber Security: Threat Prognosis (20)
Systems Thinking on a National Level, Part 2Drew David.docx

Systems Thinking on a National Level, Part 2Drew David.docx
Healthcare Attorneys Feel the Healthcare Industry Is More Vulnerable to Cyber...

Healthcare Attorneys Feel the Healthcare Industry Is More Vulnerable to Cyber...
Big data and cyber security legal risks and challenges

Big data and cyber security legal risks and challenges
Reasons for the Popularity of Medical Record Theft

Reasons for the Popularity of Medical Record Theft
Running head Information security threats 1Information secur.docx

Running head Information security threats 1Information secur.docx
Cyber Risk in Healthcare Industry- Are you Protected? 

Cyber Risk in Healthcare Industry- Are you Protected?
Running Head INFORMATION SECURITY VULNERABILITY 2.docx

Running Head INFORMATION SECURITY VULNERABILITY 2.docx
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...
INCIDENT RESPONSE PLAN FOR A SMALL TO MEDIUM SIZED HOSPITAL

INCIDENT RESPONSE PLAN FOR A SMALL TO MEDIUM SIZED HOSPITAL
How to secure information systemsSolutionAnswerInformation.pdf

How to secure information systemsSolutionAnswerInformation.pdf
White Paper :- Spear-phishing, watering hole and drive-by attacks :- The New ...

White Paper :- Spear-phishing, watering hole and drive-by attacks :- The New ...
Plus de FireEye, Inc.
Plus de FireEye, Inc. (20)
Asia Pacific & The Security Gap: Don't Stand Still

Asia Pacific & The Security Gap: Don't Stand Still
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach

FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach
Dernier
College Call Girls Dehradun Kavya 🔝 7001305949 🔝 📍 Independent Escort Service...

College Call Girls Dehradun Kavya 🔝 7001305949 🔝 📍 Independent Escort Service...Call Girls Lucknow Aaradhya 9719455033 Independent Escort Service Lucknow
Call Girls Guwahati Aaradhya 👉 7001305949👈 🎶 Independent Escort Service Guwahati

Call Girls Guwahati Aaradhya 👉 7001305949👈 🎶 Independent Escort Service GuwahatiCall Girls Lucknow Aaradhya 9719455033 Independent Escort Service Lucknow
Call Girl Chandigarh Mallika ❤️🍑 9907093804 👄🫦 Independent Escort Service Cha...

Call Girl Chandigarh Mallika ❤️🍑 9907093804 👄🫦 Independent Escort Service Cha...High Profile Call Girls Chandigarh Aarushi
VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow

VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service LucknowCall Girls Lucknow Aaradhya 9719455033 Independent Escort Service Lucknow
Russian Call Girls South Delhi 9711199171 discount on your booking

Russian Call Girls South Delhi 9711199171 discount on your bookingRussian Escorts Delhi | 9711199171 | To Enjoy Every Moments Of Life!
Dernier (20)
Gurgaon iffco chowk 🔝 Call Girls Service 🔝 ( 8264348440 ) unlimited hard sex ...

Gurgaon iffco chowk 🔝 Call Girls Service 🔝 ( 8264348440 ) unlimited hard sex ...
Book Call Girls in Noida Pick Up Drop With Cash Payment 9711199171 Call Girls

Book Call Girls in Noida Pick Up Drop With Cash Payment 9711199171 Call Girls
Call Girls Gurgaon Vani 9999965857 Independent Escort Service Gurgaon

Call Girls Gurgaon Vani 9999965857 Independent Escort Service Gurgaon
Call Girls Service Bommasandra - Call 7001305949 Rs-3500 with A/C Room Cash o...

Call Girls Service Bommasandra - Call 7001305949 Rs-3500 with A/C Room Cash o...
College Call Girls Dehradun Kavya 🔝 7001305949 🔝 📍 Independent Escort Service...

College Call Girls Dehradun Kavya 🔝 7001305949 🔝 📍 Independent Escort Service...
College Call Girls Hyderabad Sakshi 9907093804 Independent Escort Service Hyd...

College Call Girls Hyderabad Sakshi 9907093804 Independent Escort Service Hyd...
Call Girls Guwahati Aaradhya 👉 7001305949👈 🎶 Independent Escort Service Guwahati

Call Girls Guwahati Aaradhya 👉 7001305949👈 🎶 Independent Escort Service Guwahati
Call Girls Kukatpally 7001305949 all area service COD available Any Time

Call Girls Kukatpally 7001305949 all area service COD available Any Time
Call Girl Chandigarh Mallika ❤️🍑 9907093804 👄🫦 Independent Escort Service Cha...

Call Girl Chandigarh Mallika ❤️🍑 9907093804 👄🫦 Independent Escort Service Cha...
Housewife Call Girls Nandini Layout - Phone No 7001305949 For Ultimate Sexual...

Housewife Call Girls Nandini Layout - Phone No 7001305949 For Ultimate Sexual...
VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow

VIP Call Girls Lucknow Isha 🔝 9719455033 🔝 🎶 Independent Escort Service Lucknow
Russian Call Girls in Raipur 9873940964 Book Hot And Sexy Girls

Russian Call Girls in Raipur 9873940964 Book Hot And Sexy Girls
Call Girl Service ITPL - [ Cash on Delivery ] Contact 7001305949 Escorts Service![Call Girl Service ITPL - [ Cash on Delivery ] Contact 7001305949 Escorts Service](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Call Girl Service ITPL - [ Cash on Delivery ] Contact 7001305949 Escorts Service](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Call Girl Service ITPL - [ Cash on Delivery ] Contact 7001305949 Escorts Service
9711199012 Najafgarh Call Girls ₹5.5k With COD Free Home Delivery

9711199012 Najafgarh Call Girls ₹5.5k With COD Free Home Delivery
Russian Call Girls South Delhi 9711199171 discount on your booking

Russian Call Girls South Delhi 9711199171 discount on your booking
Call Girls Hyderabad Krisha 9907093804 Independent Escort Service Hyderabad

Call Girls Hyderabad Krisha 9907093804 Independent Escort Service Hyderabad
Russian Escorts Delhi | 9711199171 | all area service available

Russian Escorts Delhi | 9711199171 | all area service available
[Infographic] Healthcare Cyber Security: Threat Prognosis
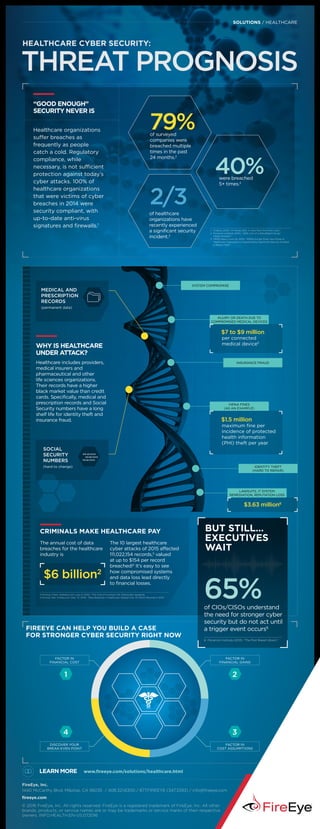
- 1. FireEye, Inc. 1440 McCarthy Blvd. Milpitas, CA 95035 / 408.321.6300 / 877.FIREEYE (347.3393) / info@fireeye.com fireeye.com © 2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.HEALTH.EN-US.072016 Learn More www.fireeye.com/solutions/healthcare.html THREAT PROGNOSIS Healthcare Cyber Security: Healthcare organizations suffer breaches as frequently as people catch a cold. Regulatory compliance, while necessary, is not sufficient protection against today’s cyber attacks. 100% of healthcare organizations that were victims of cyber breaches in 2014 were security compliant, with up-to-date anti-virus signatures and firewalls.1 “Good enough” security never is 1 FireEye (2015). "M-Trends 2015: A View from the Front Lines." 2 Ponemon Institute (2015). "2015 Cost of a Data Breach Study: Global Analysis." 3 HIMSS News (June 30, 2015). "HIMSS Survey Finds Two-Thirds of Healthcare Organizations Experienced a Significant Security Incident in Recent Past." 79%of surveyed companies were breached multiple times in the past 24 months.2 40%were breached 5+ times.2 of healthcare organizations have recently experienced a significant security incident.3 2/3 solutions / HEALTHCARE Why is Healthcare Under Attack? Medical and prescription records (permanent data) Social Security numbers (hard to change) System compromise Injury or death due to compromised medical devices INSURANCE FRAUD HIPAA FINES (as an example) Identity theft (hard to repair) Lawsuits, IT system remediation, reputation loss per connected medical device5 $7 to $9 million maximum fine per incidence of protected health information (PHI) theft per year $1.5 million FireEye can help you build a case for stronger cyber security right now 1 2 Factor in financial cost 34 475-45-XXXX 341-66-XXXX $3.63 million6 176-82-XXXX But Still… Executives Wait of CIOs/CISOs understand the need for stronger cyber security but do not act until a trigger event occurs6 65% 6 Ponemon Institute (2013). "The Post Breach Boom." The annual cost of data breaches for the healthcare industry is Criminals Make Healthcare Pay 4 Partnoy, Frank. Globalist.com (July 21, 2012). "The Cost of a Human Life, Statistically Speaking. 5 Munroe, Dan. Forbes.com (Dec. 31, 2015). "Data Breaches in Healthcare Totaled Over 112 Million Records in 2015." $6 billion2 The 10 largest healthcare cyber attacks of 2015 affected 111,022,154 records,5 valued at up to $154 per record breached!2 It’s easy to see how compromised systems and data loss lead directly to financial losses. Factor in financial gains Factor in cost assumptions Discover your break-even point Healthcare includes providers, medical insurers and pharmaceutical and other life sciences organizations. Their records have a higher black market value than credit cards. Specifically, medical and prescription records and Social Security numbers have a long shelf life for identity theft and insurance fraud.
