Usb port visibility controller poster
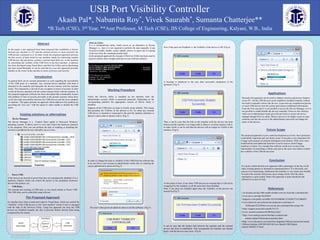
- 1. RESEARCH POSTER PRESENTATION DESIGN © 2012 www.PosterPresentations.com In this paper a new approach have been proposed that establishes a barrier between any machine or P.C and the external devices or more precisely the USB devices connected to it. In other words the proposed approach prevents the free access of data stored in any machine simply by connecting random USB devices like pen-drives, printers, external hard disks etc; to the machine by controlling the visibility of the USB Ports to the host machine. A software has been developed using Visual Basic and DevCon Utility and its functioning has been tested thereafter. It can be said that in a way this approach provides benefits to the owner of the machine in terms of privacy and security. Abstract Introduction • Device Manager- The Device Manager is a Control Panel applet in Microsoft Windows operating systems. It allows users to view and control the hardware attached to the computer. Here one can perform the task of enabling or disabling the external or peripheral devices manually one at a time. • Power USB- If the devices are devoid of power then they are automatically disabled. It is a hardware solution which can control the power to the peripheral electronic devices like printers, etc. • USB Relay- The concept and working of USB relay is very much similar to Power USB. The USB relay can be controlled using software. Existing solutions or alternatives Firstly the Devcon utility is installed on the machine from the administrator account which is password protected. Depending on the corresponding platform the appropriate version of Devon utility is installed. Suppose all the USB ports are kept in Enable mode initially. This means that presently the Visibility of the devices is On. So when any external USB device is inserted or connected to the port the machine identifies or detects it and is able to interact with it. (Fig 1) In order to change the state or visibility of the USB Ports the software has to be run from a user account in administrator mode only, by entering the correct administrator password (Fig 2) The user is then given an option to enter or exit the software. (Fig 3). Working Procedure Conclusion It is quite evident that this new approach offers advantages in the face of all other existing options or alternatives mentioned above. It is obviously very precise in its functioning, furthermore the interface is very much user friendly. It ensures the security and privacy up to a large extent. Also the entire mechanism is quite simple. Hence this approach is quite beneficial and efficient in its area of work. References 1.en.kioskea.net/faq/1886-enable-disable-a-device-from-the-command-line 2.www.devx.com/tips/Tip/42644 3.digital.ni.com/public.nsf/allkb/1D120A90884C25AF862573A7006029 4.www.daniweb.com/software-development/visual-basic-4- 56/threads/423258/how-to-execute-dos-command-line-using-vb6 5.http://support.microsoft.com/kb/311272 6.www .pwrusb.com/powerUSB-basic.html 7.http://www.analog.com/en/interface-isolation/usb- isolators/adum4160/products/product.html 8.http://www.aliexpress.com/item/free-shipping-USB-port-protection-board- USB-port-Isolator-ADUM4160-Full-Low-Speed-USB-Digital- Isolator/508402173.html Applications Presently this approach can be used to enhance security and privacy features of any P.C. All the USB devices can be enabled or disabled instantly without the need to manually remove the devices. It prevents any unauthorised person to insert USB devices into the system and extract confidential information. From the User account it is not possible to access the Device Manager, so it is not possible to enable/disable the devices manually. However this software when run in administrator mode gives the provision to access the device manager though DevCon utility. Hence it proves to be highly secure as only someone who has the access to the administrator password can change the status of the devices. *B.Tech (CSE), 3rd Year, **Asst Professor, M.Tech (CSE), JIS College of Engineering, Kalyani, W.B., India Akash Pal*, Nabamita Roy*, Vivek Saurabh*, Sumanta Chatterjee** USB Port Visibility Controller The Proposed Approach In general there are no security parameters as such regarding the accessibility of the USB ports of a machine. Any external device attached with them is detected by the machine and thereafter the devices interact with the machine freely. This interaction is devoid of any exception in terms of security in other words all devices attached with the system interact freely with the machine. In the proposed approach software has been developed that considerably lessens this problem of lack of security prevalent in the present scenario where there exists free data accessibility between the USB devices and the host computer or machine. This paper presents an approach which addresses this problem by providing the ‘host user’ with the option to either enable or disable the USB ports. An interface have been created and coded in Visual Basic which can control the ‘Visibility’ of the USB devices to the ‘host machine’ which in turn is managed with the help of the DevCon Utility. Using this approach not only the USB devices are disabled instantly but also it prevents further devices from being recognized by the system. Future Scope The proposed approach is just a small development as of now, but it possesses a potentially important and vast future scope. It can play a very important role in large scale projects of artificial intelligence and robotics. With a few more modifications and additional functions it can be used to control larger machines in future .For example this software could serve as one of the functionality of controlling a robotic arm just as the users were able to control the visibility of the USB devices here. Now if the ports are Disabled i.e. the Visibility of the device is Off. (Fig 4). A message is displayed to the user after successful completion of the operation. (Fig 5). Then it can be seen that the link on the machine with the devices has been broken and the machine is no longer able to detect it, let alone interact with it. In other words it can be said that the devices will no longer be Visible to the machine. (Fig 6). At this point of time, if any other USB devices are inserted then it will not be recognized by the machine, as all the ports have been disabled. Only if the ports are Enabled again then the Visibility of the devices are turned On (Fig 7). It can be seen that the broken link between the machine and the external devices has been re-established. And consequently the machine can interact freely with the devices once more. (Fig 8). DevCon Utility- It is a command-line utility which serves as an alternative to Device Manager i.e.; here it is not required to perform the task manually. It can be used to enable, disable, restart, update, remove or query one or a group of devices from the command prompt itself. In the proposed approach the concept of DevCon Utility has been used to present a better, more compact and easy-to-use software solution.
