Infographic under the hood of a connected car hack
•
65 j'aime•10,574 vues
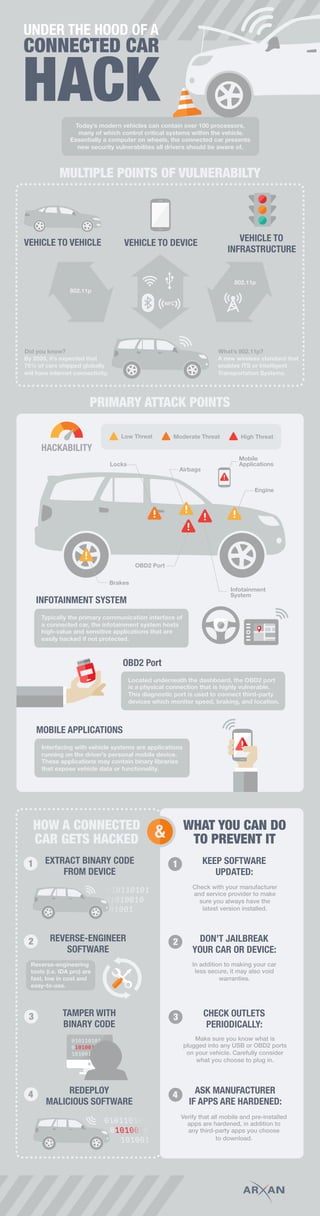
The document discusses security vulnerabilities in connected cars. Modern vehicles contain over 100 processors controlling critical systems, essentially making them computers on wheels. This presents multiple points of vulnerability, with primary attack points being the OBD2 port located under the dashboard and mobile applications interfacing with vehicle systems. Hackers can extract binary code from these systems, reverse engineer the software, and tamper with code to deploy malicious software affecting systems like the engine, brakes, or airbags. The infotainment system is also vulnerable due to hosting sensitive apps.
Signaler
Partager
Signaler
Partager
Télécharger pour lire hors ligne
Recommandé
Recommandé
Contenu connexe
Tendances
Tendances (20)
DWS15 - Connected things forum - conclusive keynote - Raj Talluri

DWS15 - Connected things forum - conclusive keynote - Raj Talluri
Autonomous Driving: Philosophical Changes in Insurance and Public Readiness

Autonomous Driving: Philosophical Changes in Insurance and Public Readiness
Ericsson ConsumerLab – Wearable technology and the internet of things 

Ericsson ConsumerLab – Wearable technology and the internet of things
The Challenge of Managing & Securing Data in the Mobile World. By Stuart Chev...

The Challenge of Managing & Securing Data in the Mobile World. By Stuart Chev...
Realizing the Promise of the Mobile Workforce through a Mobile Device Platfor...

Realizing the Promise of the Mobile Workforce through a Mobile Device Platfor...
Connected Cars - Poster Child for the IoT Reality Check

Connected Cars - Poster Child for the IoT Reality Check
Oies_IoT_week_lisbon_201506_wearablesfieldservice_final

Oies_IoT_week_lisbon_201506_wearablesfieldservice_final
New Technology - our opportunities in the meeting industry

New Technology - our opportunities in the meeting industry
AI/Artificial Intelligent in Aviation Beyond Covid 19

AI/Artificial Intelligent in Aviation Beyond Covid 19
Rio Info 2015 - Projetos de Big Data no Setor Público - Karin Breitman

Rio Info 2015 - Projetos de Big Data no Setor Público - Karin Breitman
Similaire à Infographic under the hood of a connected car hack
Similaire à Infographic under the hood of a connected car hack (20)
Countering Cybersecurity Risk in Today's IoT World

Countering Cybersecurity Risk in Today's IoT World
Seminar topic -ROLE OF CYBER SECURITY IN CON CAR.pptx

Seminar topic -ROLE OF CYBER SECURITY IN CON CAR.pptx
WHITE PAPER▶ Building Comprehensive Security Into Cars

WHITE PAPER▶ Building Comprehensive Security Into Cars
Advancements and Hurdles in the Evolution of Automotive Wireless Interfaces: ...

Advancements and Hurdles in the Evolution of Automotive Wireless Interfaces: ...
Hacking your Connected Car: What you need to know NOW

Hacking your Connected Car: What you need to know NOW
Is cybersecurity protection of commercial vehicles harder?

Is cybersecurity protection of commercial vehicles harder?
Alexander Olenyev & Andrey Voloshin - Car Hacking: Yes, You can do that!

Alexander Olenyev & Andrey Voloshin - Car Hacking: Yes, You can do that!
Plus de IBM Security
Plus de IBM Security (20)
Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...

Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...
Bridging the Gap between Privacy and Security: Using Technology to Manage Com...

Bridging the Gap between Privacy and Security: Using Technology to Manage Com...
The Resilient End-of-Year Review: The Top Cyber Security Trends in 2018 and P...

The Resilient End-of-Year Review: The Top Cyber Security Trends in 2018 and P...
Leveraging Validated and Community Apps to Build a Versatile and Orchestrated...

Leveraging Validated and Community Apps to Build a Versatile and Orchestrated...
Accelerating SOC Transformation with IBM Resilient and Carbon Black

Accelerating SOC Transformation with IBM Resilient and Carbon Black
How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration

How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration
Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence

Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence
Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...

Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...
Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...

Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...
Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...

Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...
How to Improve Threat Detection & Simplify Security Operations

How to Improve Threat Detection & Simplify Security Operations
Orchestrate Your Security Defenses; Protect Against Insider Threats 

Orchestrate Your Security Defenses; Protect Against Insider Threats
Dernier
Call Girl Nashik Indira Call Now: 8617697112 Nashik Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Nashik Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Nashik understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Nashik Call Now 8617697112 Nashik Escorts 24x7

(INDIRA) Call Girl Nashik Call Now 8617697112 Nashik Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Call Girl Surat Indira: Call Now: 8250077686 Surat Escorts Booking Contact Details WhatsApp Chat: +91-8250077686 Surat Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus, they look fabulously elegant, making an impression. Independent Escorts Surat understands the value of confidentiality and discretion; they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide:(INDIRA) Call Girl Surat Call Now 8250077686 Surat Escorts 24x7

(INDIRA) Call Girl Surat Call Now 8250077686 Surat Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Call Girls Service Jammu Ishita Call Now: 8617697112 Jammu Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Jammu Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Jammu understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(ISHITA) Call Girls Service Jammu Call Now 8617697112 Jammu Escorts 24x7

(ISHITA) Call Girls Service Jammu Call Now 8617697112 Jammu Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Ready to tint your ride? Know the rules first! In many places, like California, you can tint the top 4 inches of your windshield with non-reflective film, while side and rear windows have different light transmission limits. Always check your local regulations to ensure your window tints are legal and safe.Stay Cool and Compliant: Know Your Window Tint Laws Before You Tint

Stay Cool and Compliant: Know Your Window Tint Laws Before You TintBisnar Chase Personal Injury Attorneys
Dernier (20)
8377087607, Door Step Call Girls In Majnu Ka Tilla (Delhi) 24/7 Available

8377087607, Door Step Call Girls In Majnu Ka Tilla (Delhi) 24/7 Available
(INDIRA) Call Girl Nashik Call Now 8617697112 Nashik Escorts 24x7

(INDIRA) Call Girl Nashik Call Now 8617697112 Nashik Escorts 24x7
Is Your Volvo XC90 Displaying Anti-Skid Service Required Alert Here's Why

Is Your Volvo XC90 Displaying Anti-Skid Service Required Alert Here's Why
Somya Surve Escorts Service Bilaspur ❣️ 7014168258 ❣️ High Cost Unlimited Har...

Somya Surve Escorts Service Bilaspur ❣️ 7014168258 ❣️ High Cost Unlimited Har...
Marathi Call Girls Santacruz WhatsApp +91-9930687706, Best Service

Marathi Call Girls Santacruz WhatsApp +91-9930687706, Best Service
Why Does My Porsche Cayenne's Exhaust Sound So Loud

Why Does My Porsche Cayenne's Exhaust Sound So Loud
Call Girls In Kotla Mubarakpur Delhi ❤️8448577510 ⊹Best Escorts Service In 24...

Call Girls In Kotla Mubarakpur Delhi ❤️8448577510 ⊹Best Escorts Service In 24...
Madiwala Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore Es...

Madiwala Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore Es...
(INDIRA) Call Girl Surat Call Now 8250077686 Surat Escorts 24x7

(INDIRA) Call Girl Surat Call Now 8250077686 Surat Escorts 24x7
Is Your BMW PDC Malfunctioning Discover How to Easily Reset It

Is Your BMW PDC Malfunctioning Discover How to Easily Reset It
(ISHITA) Call Girls Service Jammu Call Now 8617697112 Jammu Escorts 24x7

(ISHITA) Call Girls Service Jammu Call Now 8617697112 Jammu Escorts 24x7
+971565801893>>SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN ABUDHABI,DUBAI MA...

+971565801893>>SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN ABUDHABI,DUBAI MA...
Vip Mumbai Call Girls Mira Road Call On 9920725232 With Body to body massage ...

Vip Mumbai Call Girls Mira Road Call On 9920725232 With Body to body massage ...
Stay Cool and Compliant: Know Your Window Tint Laws Before You Tint

Stay Cool and Compliant: Know Your Window Tint Laws Before You Tint
Majestic Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore Es...

Majestic Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore Es...
Call Girls Hongasandra Just Call 👗 7737669865 👗 Top Class Call Girl Service B...

Call Girls Hongasandra Just Call 👗 7737669865 👗 Top Class Call Girl Service B...
Bangalore Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore E...

Bangalore Call Girls: 🍓 7737669865 🍓 High Profile Model Escorts | Bangalore E...
➥🔝 7737669865 🔝▻ Bhiwandi Call-girls in Women Seeking Men 🔝Bhiwandi🔝 Escor...

➥🔝 7737669865 🔝▻ Bhiwandi Call-girls in Women Seeking Men 🔝Bhiwandi🔝 Escor...
Call Girls in Malviya Nagar Delhi 💯 Call Us 🔝9205541914 🔝( Delhi) Escorts Ser...

Call Girls in Malviya Nagar Delhi 💯 Call Us 🔝9205541914 🔝( Delhi) Escorts Ser...
Infographic under the hood of a connected car hack
- 1. CONNECTED CAR HACK UNDER THE HOOD OF A new security vulnerabilites all drivers should be aware of. Today’s modern vehicles can contain over 100 processors, many of which control critical systems within the vehicle. Essentially a computer on wheels, the connected car presents MULTIPLE POINTS OF VULNERABILTY PRIMARY ATTACK POINTS CAR GETS HACKED devices which monitor speed, braking, and location. Located underneath the dashboard, the OBD2 port is a physical connection that is highly vulnerable. This diagnostic port is used to connect third-party OBD2 Port that expose vehicle data or functionality. Interfacing with vehicle systems are applications running on the driver’s personal mobile device. These applications may contain binary libraries MOBILE APPLICATIONS Infotainment Engine Locks Brakes System Airbags OBD2 Port EXTRACT BINARY CODE FROM DEVICE REVERSE-ENGINEER SOFTWARE TAMPER WITH BINARY CODE REDEPLOY MALICIOUS SOFTWARE High ThreatModerate ThreatLow Threat Mobile Applications 1 2 3 4 easily hacked if not protected. Typically the primary communication interface of a connected car, the infotainment system hosts high-value and sensitive applications that are INFOTAINMENT SYSTEM 1 & 2 3 4 KEEP SOFTWARE UPDATED: DON’T JAILBREAK YOUR CAR OR DEVICE: CHECK OUTLETS PERIODICALLY: ASK MANUFACTURER IF APPS ARE HARDENED: TO PREVENT IT WHAT YOU CAN DOHOW A CONNECTED HACKABILITY Check with your manufacturer and service provider to make sure you always have the In addition to making your car less secure, it may also void warranties. what you choose to plug in. Make sure you know what is plugged into any USB or OBD2 ports on your vehicle. Carefully consider latest version installed. to download. Verify that all mobile and pre-installed apps are hardened, in addition to any third-party apps you choose VEHICLE TO VEHICLE VEHICLE TOVEHICLE TO DEVICE NFC 802.11p 802.11p INFRASTRUCTURE What’s 802.11p? A new wireless standard that enables ITS or Intelligent Transportation Systems. Did you know? By 2020, it’s expected that 75% of cars shipped globally will have internet connectivity. Reverse-engineering tools (i.e. IDA pro) are fast, low in cost and easy-to-use.
